New capabilities for Azure monitoring allow you to ‘bring you own’ SIEM (security information and event management) and connect to Azure log and event data streams.
Azure as a data provider
I’d call it a landmark achievement for Azure: Enough enterprise customers are relying on Azure AD for business critical identity and security services that’s there’s a market to feed that data back to those customers for integration with their enterprise security solution(s). We generally think of Azure as a ‘destination’ platform for data analytics, but if you are not ‘all in Azure’ that should not preclude you from using the ‘best of Azure’ services as they benefit your organization.
Azure AD is the gateway to Office365 where much of commerce takes place. Adding high-fidelity and even pro-active monitoring of Azure AD is a requisite part of a modern security portfolio. If you are ‘all in Azure’ the Azure Security Center and options like Azure Log Analytics rather than Splunk, or Microsoft Intelligent Security Graph are in play. But if customers are just using some Azure services like Azure AD and Azure monitor, a way to tie the Azure pieces back into a customer management solution is a winner all around.
Partner solutions using Azure Monitor
Microsoft recently released a set of instructions that allow you to connect your SIEM on premises on in any cloud using Azure event hub: Stream Azure monitoring data to an event hub for consumption by an external tool. There is an animation of how this works at YouTube: https://youtu.be/SPHxCgbcvSw (Figure 1 below from the Microsoft video.)
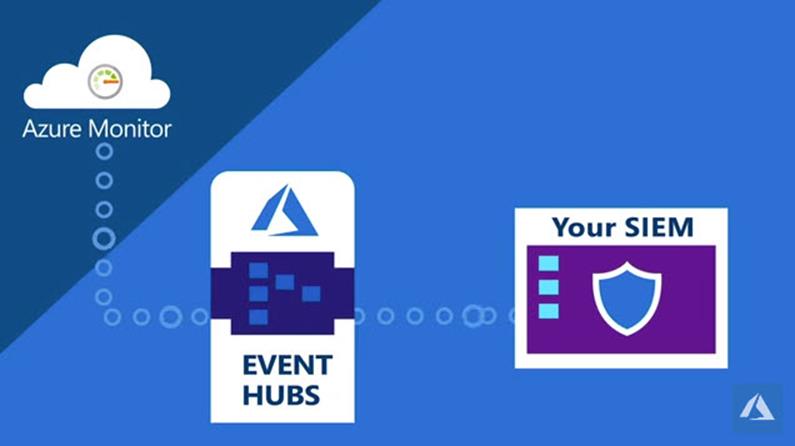
Figure 1 – Connect your SIEM to Azure Monitor via Event hubs
Most any data available in Azure monitoring can be sent into an event hub where it can be pulled into a partner tool. Think: Application, Guest OS, Azure resource, Azure subscription, and Azure tenant monitoring data. A use case for Azure AD audit data in a customer SIEM is: Early alerting that an employee Office 365 account is under brute force attack, evidenced by a high number of failed login attempts over a given time.
Supported SIEM Tools
There are currently three (3) supported SIEM tools that integrate with Azure activity logs:
Splunk
Integrate Azure AD logs with Splunk by using Azure Monitor (preview)
Sumologic
Integrate Azure AD logs with SumoLogic by using Azure Monitor (preview)
IBM QRadar
IBM QRadar: The DSM and Azure Event Hub Protocol
At each of the links above you will find instructions to add Azure monitor events streams using Azure event hub to the respective SIEM tool.
Bring your own SIEM
This technology supports Microsoft goals of ‘going where the customer is’ when it comes to cloud services. A modern enterprise needs to add Azure AD login monitoring to their security model as surely as traditional Active Directory login (i.e. Kerberos) analysis has been a mainstay of SIEMs for a few decades. Now there is the option to ‘keep what you have’ in terms of SIEM and start benefiting from insight into Azure AD activities and operations immediately.
Tags: #MVPBuzz #AzureAD #ActiveDirectory #Splunk #Sumologic #QRadar #AzureMonitor #SIEM #netadmin
