At Microsoft’s Virtual Ignite 2020 conference this week, a recent technology took center stage: Azure Arc. Part of the Azure Hybrid solution, Azure Arc is a concept and an agent technology, based on well understood Desired State Configuration (DSC) tools, that extends Azure management features to on-premises or other-cloud Windows and Linux computers. You can think of Azure Arc as a ‘management platform as a service’ solution, hosted by Microsoft as a free PaaS service.
Microsoft refers to the management layer where Azure Arc lives as the Control plane and it’s happy to share it with you. Azure Arc adds no additional cost to your Azure bill. For free you can use just the default Control plane functions such as tags and role-based access control (RBAC). However, the value from Azure Arc arises when you use Azure Policy to deploy other agents and services–like Azure Monitor, Azure Sentinel, and Backup—via Azure Arc. Figure 1 below illustrates how Azure Arc provides free control plane services (left) and provides the delivery mechanism for à la carte services as you see fit (right). You’ll pay for the actual services you consume, and not pay for the “plumbing” to deliver the services.
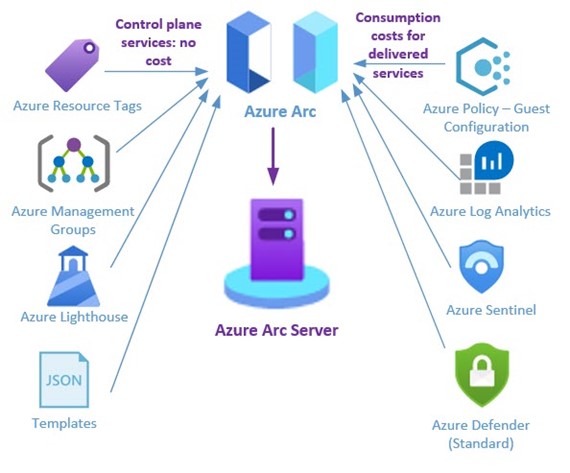
Figure 1 – Azure Arc is an extension of the Azure control plane, running in your on-premises datacenter or other cloud.
While a seemingly small cog in the giant IT machine, Azure Arc seeks once and for all to end the dilemma that network owners and service providers have faced for decades: Managing multiple agents for multiple management services at scale. This article is a deep dive into using Azure Arc to get a big job done easily, specifically, we install an Azure Arc agent on a new non-Azure computer, then configure that Azure Arc computer to pull down other management agents and enable security policies, saving a lot of time and hassle.
|
Note: Azure Arc enables hybrid management to a variety of technologies, such as Kubernetes clusters, but this article just focuses on using Azure Arc to manage non-Azure computers. |
The Azure Control Plane and You
The heart of Azure Arc is Azure Policy, which is a means to deploy DSC-like configuration settings in JSON format that can be associated with Azure objects. The global hyper-scale Azure cloud itself is managed by Azure Resource Manager, sometimes written as Azure RM or ARM. ARM is the technology within the Azure platform which is responsible for provisioning resources. ARM uses JSON format notation to do everything—it’s not inaccurate to view the entire Azure cloud as a giant living JSON document. Figure 2 shows you what an Azure policy looks like—a JSON-based definition, in this case one that deploys the Log Analytics agent to a Windows Azure Arc computer.
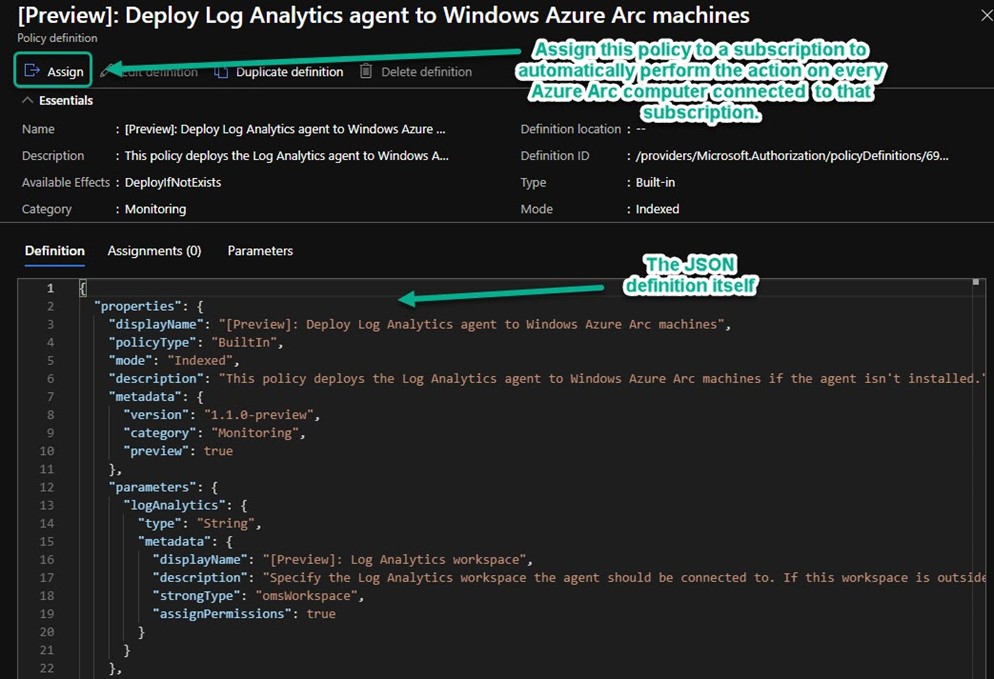
Figure 2 – An Azure policy definition: It’s a JSON document that you assign to a subscription, resource group, or management group.
Making Azure Yours
Azure Policy is how you can insert your organizational policies and settings into the fabric of Azure resource management. Many Azure customers have discovered Azure Policy and are using it to standardize deployments and achieve configuration consistency across their enterprise, which might include many Azure subscriptions in many regions—All sharing the identical policies. This particularly applies to organizations that need to comply with a regulatory framework, such as PCI-DSS or HIPAA. Any investment your organization has in selecting and customizing JSON policy definitions for your Azure VMs can now be applied consistently to all your computers, everywhere. This is a huge time saver and provides the standardization and governance features every large organization seeks.
Azure Arc Use Cases
- Azure Arc has value for current Azure customers that want to extend the effective cloud management tools already in use in Azure to their on-premise datacenters and other-cloud environments like AWS or Google Cloud Platform. In that scenario, the Azure Portal’s Policy Compliance blade (seen in Figure 3) becomes the ‘single pane of glass’ for all computing assets which is very appealing come audit time.
-
Another type of customer that should consider Azure Arc may be new to Azure, but is deploying the Azure Sentinel SIEM across their enterprise. Azure Sentinel uses the Azure Log Analytics agent and as a best practice includes Azure Defender – Standard (Azure Security Center) integration. Azure Arc is the ideal way to roll out the management agent portion of an enterprise Azure Sentinel deployment.
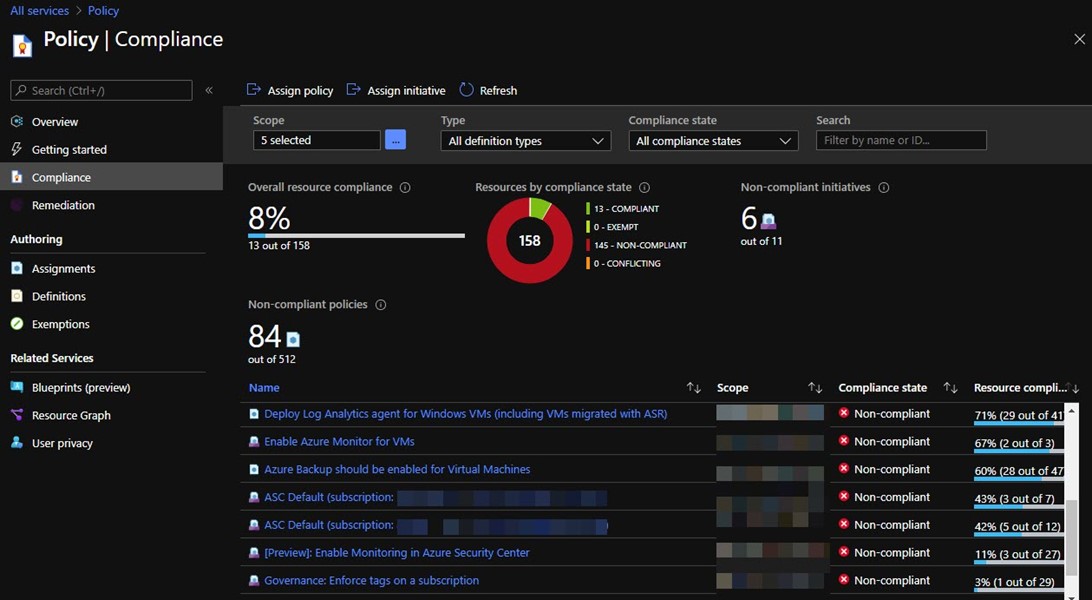
Figure 3 – The Policy Compliance blade in the Azure portal rolls up the status of all your Azure and Azure Arc computers, both Windows and Linux.
Installing the Azure Arc Agent
At installation time, the Azure Connected Machine Agent needs to authenticate with Azure AD to validate the new Azure Arc computer is authorized to be associated with your Azure subscription. It can do this two ways:
- Add servers manually with an interactive script. This is suitable for small deployments and testing. You log into Azure with your individual user credential for each install. This article steps through this method.
- Add servers at scale. This method uses the identity and client secret (application password) of an Azure App Registration that you create in your Azure AD. Run the agent install with switches via any scripting or management tool you like.
Add Azure Arc servers using interactive script
(1) In your Azure portal, push New and select Azure Arc for servers, then push Create.
(2) At the Select a method blade seen in Figure 4, push Generate script.
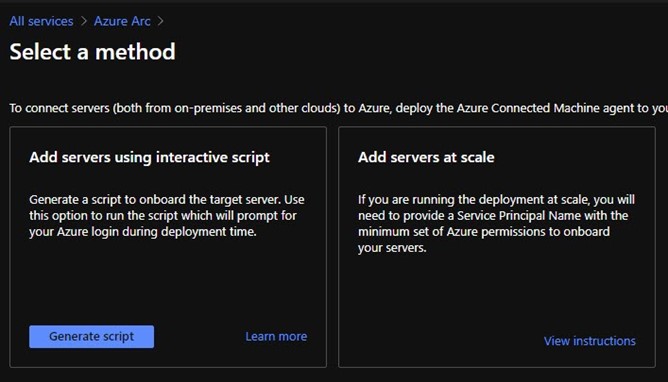
Figure 4 – There are two primary ways to connect servers on-premises and in other clouds to Azure.
(3) Enter the Resource details and Tags appropriate for your environment, then push Download and run script to arrive at the blade seen in Figure 5.
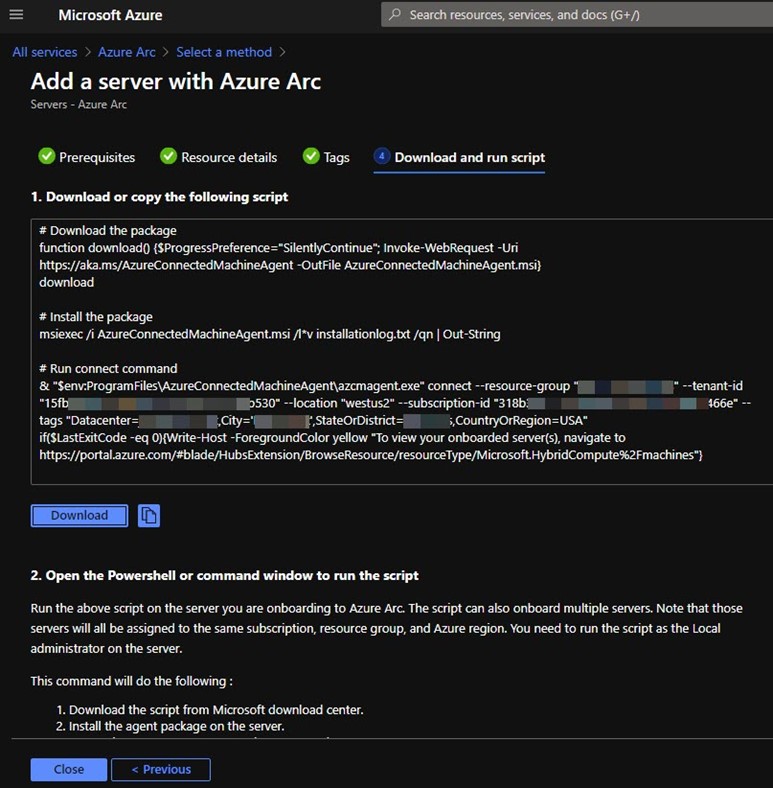
Figure 5 – The Azure portal will automatically generate a custom script that onboards a computer to Azure Arc.
(4) Download the script (OnboardingScript.ps1) and copy it to the server you are adding to Azure Arc.
- Run the script in an elevated PowerShell session. Note the code the script prints out.
- Open a web browser to https://microsoft.com/devicelogin.
- Login with an Azure AD credential in your tenant and enter the code as shown in Figure 6.
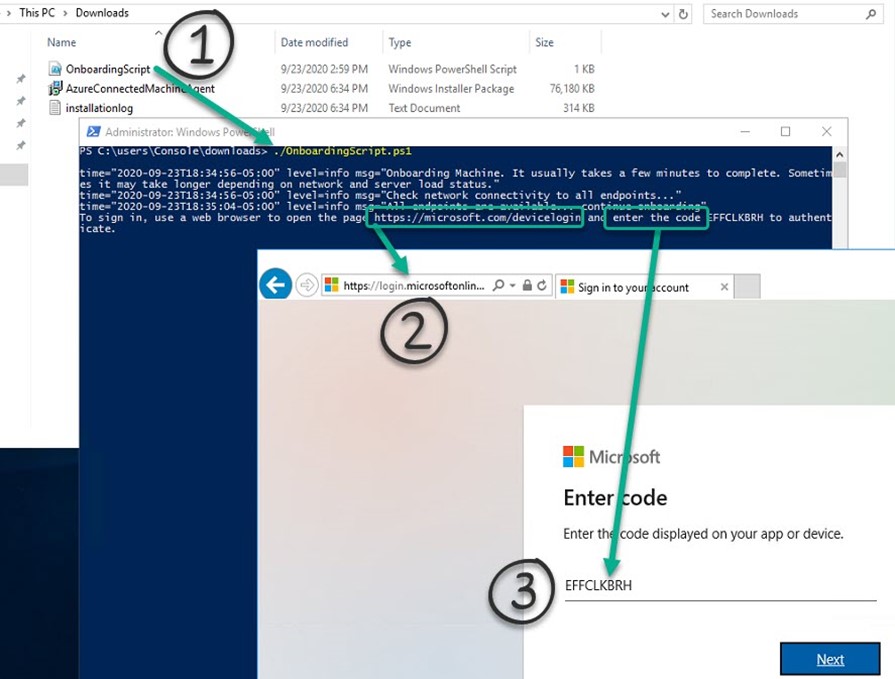
Figure 6 – Three steps to install the Azure Arc agent manually with onboarding script.
Notice in Figure 6 that the script will download the AzureConnectedMachineAgent Windows Installer Package to the folder where you executed the script. A log file installationlog is also created at the same location. (You have a limited time to complete login with a given code before it expires.)
(5) After you have installed the agent, you will find Azure Connected Machine Agent listed in Add/Remove Programs as shown in Figure 7.
(a) Agent files are located at C:\Program Files\AzureConnectedMachineAgent.
(b) Two Windows services are created:
- Guest Configuration Arc Service (GCArcService): This service monitors desired state of the machine.
-
Guest Configuration Extension service (ExtensionService): The service installs the requested extensions.
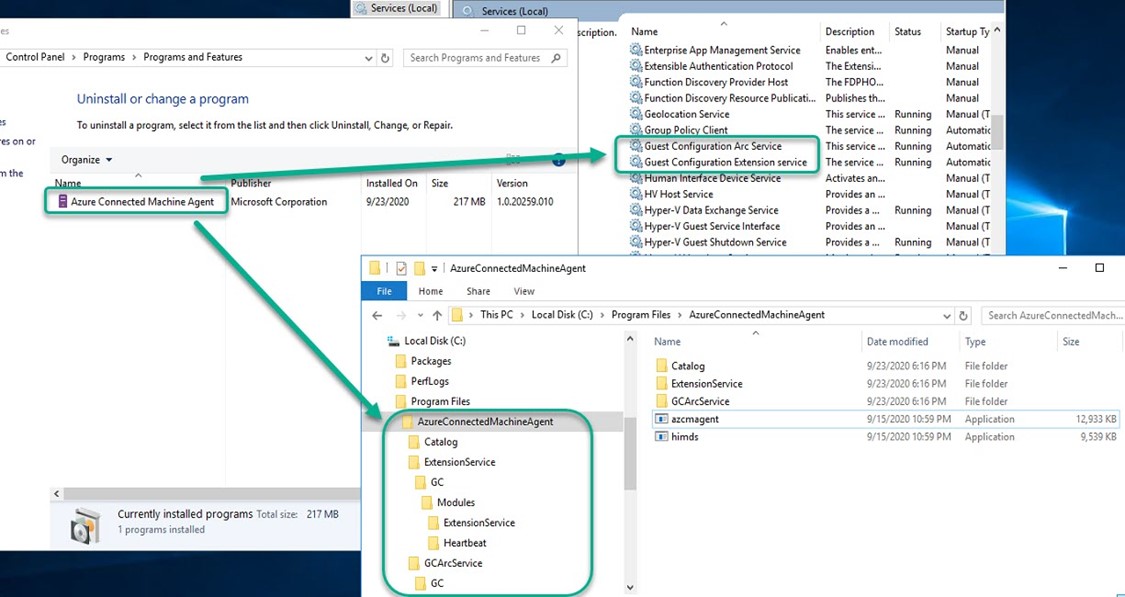
Figure 7 – Tear-down of the Azure Connected Machine Agent folders and services.
(6) After the Azure Arc agent is installed, you can open your Azure Portal to view the new hybrid computer object: https://portal.azure.com/#blade/HubsExtension/BrowseResource/resourceType/Microsoft.HybridCompute%2Fmachines. Figure 8 shows what you might see soon after adding an Azure Arc server. The Server – Azure Arc -> Operations -> Policies blade will list all the policies and initiatives that are assigned to the subscription, resource group, and management group the Azure Arc server is part of. Of particularly high value is the Enable Azure Monitor for VMs initiative. An Azure policy initiative is a collection of multiple individual Azure policy definitions that are deployed together as a group.
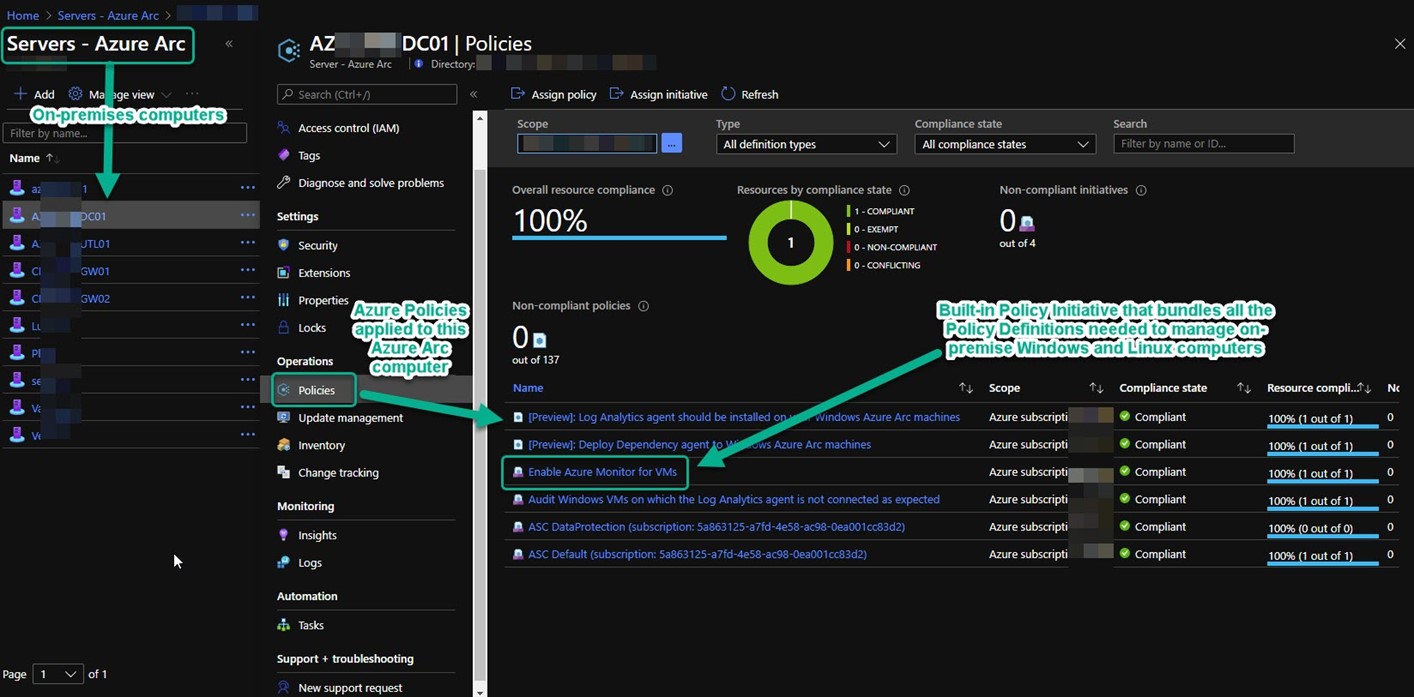
Figure 8 – The Azure portal blade for each Azure Arc server lists the status of all policies assigned to that computer.
(7) The recommended method of enabling hybrid VMs is first enabling Azure Arc for servers so that the VMs can be enabled for Azure Monitor for VMs using processes similar to Azure VMs. Figure 9 illustrates the power and efficiency of Azure Arc for servers. It’s the Enable Azure Monitor for VMs initiative. Azure Arc is going to do all the interrelated agent and agent component installs for you. You don’t need to configure or monitor anything else to achieve uniform management tool coverage of your estate—in Azure and everywhere else.
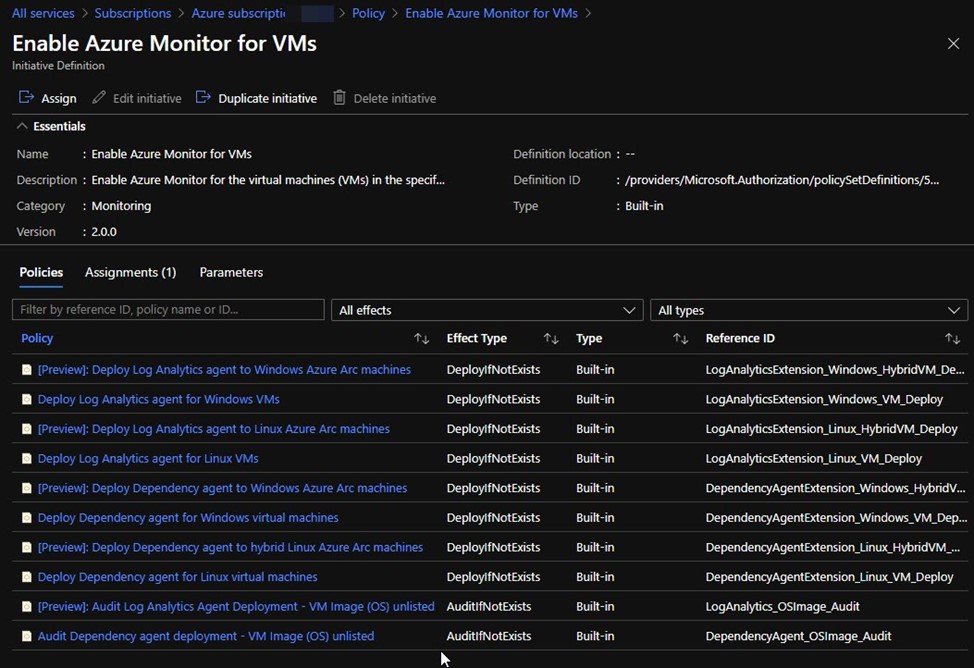
Figure 9 – Built-in Azure Policy Initiative that bundles all the policies needed to push Azure Log Analytics agents to Windows and Linux computers.
Tags: #AzureArc #AzurePolicy #MSIgnite #MVPBuzz #AzureSentinel #HybridCloud #Governance #AzureGovernance #Compliance #sysctr
