Microsoft quietly made public this week a significant new feature of their flagship Cloud Workload Protection (CWP) product for servers also known as Defender for Servers (DfS). Since the launch of Azure Security Center (ASC) in February 2018 and the rename of the product to Microsoft Defender for Cloud (DfC) in November 2021, enabling DfS plans was only possible at the Azure management group level and Azure subscription level. The new feature allows you to granularly enable or disable DfS plan coverage at the resource group or individual server level. This removes a barrier to implementation of DfS at some large organizations and provides flexibility to customers of all sizes.
Default DfS ‘all or nothing’ plan assignment assures central control
Microsoft Defender for Servers is a fantastic value and an indispensable security tool for any organization with Windows or Linux servers anywhere in the world—in public clouds like Azure, Amazon AWS, and Google GPC, and in private clouds like VMware vSphere, Azure Stack HCI, as well as any physical server. Coincident with the rename of ASC to DfC, Microsoft also split DfS into two plans: P1 and P2. DfS P1, priced at $5 per month per server, primarily extends Microsoft Defender for Endpoint protection to servers. The much more full-featured DfS P2, priced at $15 per server per month, adds many high-value features like agentless scanning, regulatory compliance, Just-in-time (JIT) VM management access, and a significant free credit towards log ingestion when using Microsoft Sentinel as your SIEM.
With the multi-cloud features of DfC and the amazing ability of Azure Arc to project non-Azure servers into the Azure control plane, it is relatively simple for even the most distributed of large enterprises to deploy DfS protection to all their servers uniformly in all environments everywhere in the world. Before the release of the new granular plan assignment feature, DfS could only be enabled at the management group or subscription level because DfC is designed to provide centralized control over the security of all resources. This ‘monolithic’ or ‘fail-safe’ approach to enabling DfS ensures that all server resources are always protected.
As seen in Figure 1, the Management -> Environment settings page in the Azure portal, Defender for Cloud blade provides no opportunity for granular assignment of protection. You must select one DfS plan (P1 or P2) and apply that setting to the entire management group or subscription. There is no option to deploy one plan to one subset of servers and another plan to a different subset. Nor is there an option to partially deploy DfS—It’s essentially an ‘all or nothing’ decision.
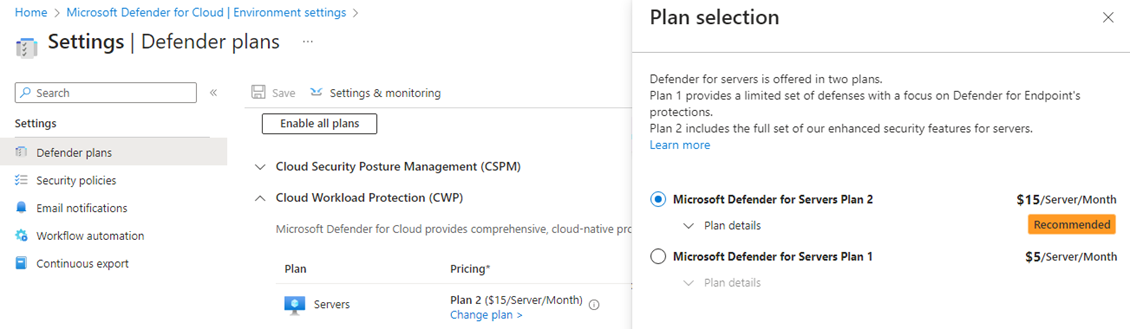
Figure 1 – Enabling Defender for Servers protection at the management group or subscription level.
One size does not fit all
While the ‘all or nothing’ approach is quite sound from a cybersecurity best practice perspective, some organizations found this aspect of DfS assignment inconvenient and in some cases even a blocker to its use. Consider a large organization with 1,000 servers in an Azure subscription. Enabling DfS P2 is a $15,000 per month investment for such a customer, and for various organizational, geographic, financial, or other considerations not all customers of that size are in a position to enable DfS given the “all or nothing” options.
Organizations ended up ‘overspending’ on more protection than they wanted–or conversely, not deploying DfS at all, with the loss of the cybersecurity protection that any deployment of DfS would have mitigated. The new granular plan assignment option for DfS allows customers to make their own assessment of the suitability of partial protection. While universal protection with DfS P2 remains the recommended best practice for most estates, customers can now perform their own due diligence and decide to possibly assume some risks and only deploy DfS to some servers, or even deploy a mix of DfS P1 and P2 in the same subscription.
How to use resource level enablement of DfS
The official name for the new granular DfS assignment feature is “resource level enablement”. That’s because you can enable DfS on two kinds of Azure resources: resource groups and servers. In fact, there are three (3) types of server resources supported for resource level enablement: Azure VMs, Azure Arc-enabled servers, and Virtual Machine Scale Sets (VMSS).
Resource level enablement of DfS is not something you can do in the Azure portal. The only supported method to enable or disable DfS at the resource level is via REST API. Fortunately, Microsoft has created an Azure PowerShell script that does everything needed to interact with the Azure API, without requiring the use of API tools such as Postman or curl.
To get started, read carefully the DfS Enablement via REST API instructions at Microsoft Learn. There are implications for the deployment of Defender for Endpoint on servers. You need to understand the sequence of events during roll out since the near real-time nature of the solution could have unintended effects involving the deployment of Defender for Endpoint. The key points to understand are these:
- Including servers in DfS P1 will trigger automatic deployment of Microsoft Defender for Endpoint (if not already deployed).
- Excluding servers from DfS P1 or P2 will also exclude them from deployment of Microsoft Defender for Endpoint (if not already deployed).
Fundamentally, resource level enablement of DfS applies in these scenarios:
- If you have already deployed DfS P2 to your subscription, resource level enablement can ‘downgrade’ selected resource groups or servers to DfS P1 or DfS “free” (which is the same as DfS disabled).
- If you want a mix of DfS “free”, P1 and/or P2, you will need to enable DfS P2 at the subscription and manage DfS “free” and/or DfS P1 by exception.
- If you have already deployed DfS P1 to your subscription, resource level enablement can ‘downgrade’ selected resource groups or servers to DfS “free”.
- If you want a mix of DfS “free” and P1, you can enable DfS P1 at the subscription and manage DfS “free” by exception.
- If you have not deployed DfS at all to your subscription, resource level enablement can ‘upgrade’ selected resource groups or servers to DfS P1.
- Optionally you can leave DfS “turned off” at the subscription and manage DfS P1 by exception.
Enablement at scale step-by-step
-
Decide which of these scenarios applies to you:
- You will enable a DfS plan for all servers in a resource group.
- You will enable a DfS plan for servers with specific tags and values anywhere in your subscription. In this case, assign the tag to the server(s) in scope for resource level enablement.
- Download the PowerShell script.
- Upload the script to a PowerShell session in Azure Cloud Shell.
-
Run the script (./ResourceLevelPricingAtScale.ps1) and when prompted paste your Azure subscription ID.
- If using the resource group method, type ‘RG‘ when prompted and type or paste the name of the resource group to be enabled.
- If using the server tag method, type ‘TAG‘ and when prompted enter the name of the tag and the tag value that indicates what server(s) are to be enabled.
- When prompted, type ‘Free‘ for DfS disabled or ‘Standard‘ for DfS P1.
- Observe the output of the script which will confirm any changes made.
Figure 2 is a condensed screenshot of an actual run of the PowerShell script. In this scenario, DfS P2 is enabled on the subscription, and we want to ‘downgrade’ one Azure Arc-enabled server to DfS P1. We pre-assigned the tag “DFCException : true” to the Azure Arc-enabled server (“Vanguard”) that we want to modify.
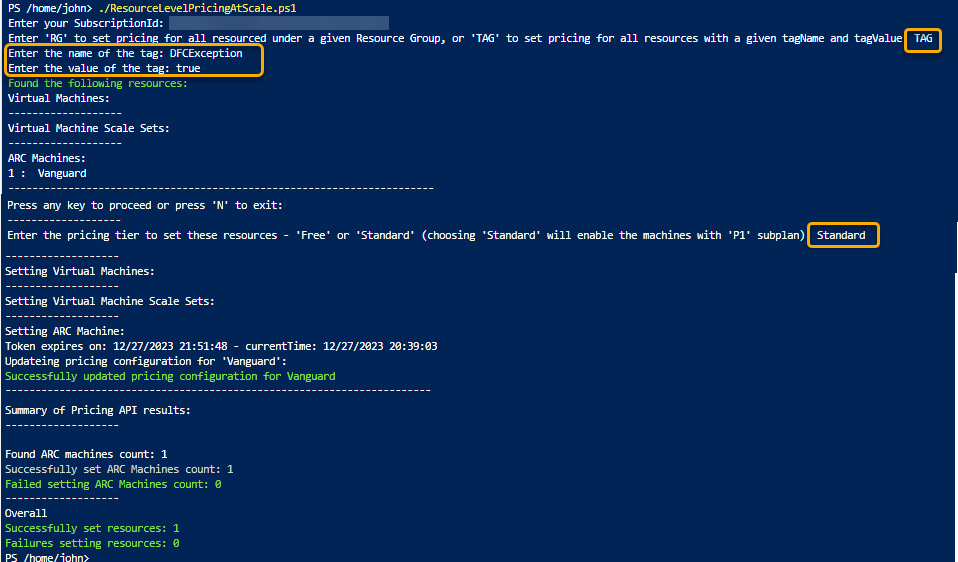
Figure 2 – Running the ResourceLevelPricingAtScale.ps1 script to ‘downgrade’ one Azure Arc-enabled server from DfS P2 to DfS P1.
Verifying DfS status changes in the Azure Portal
While you use the PowerShell script to make changes, you can verify that the changes are effective in the Azure portal. There are two places where DfS server status can be verified.
- For individual servers, the Microsoft Defender for Cloud menu item for Azure VMs and Azure VMSS, and the Security menu item for Azure Arc-enabled servers, will show the effective status: either On, Partial, or Off.
- The Defender for Cloud menu item for Inventory when filtered to Azure VMs, VMSS, or Machines – Azure Arc will show the Defender for Cloud status: either On or Off.
In addition, you can check the Activity Log of a targeted server for successful “Update pricing settings” as seen in Figure 3.
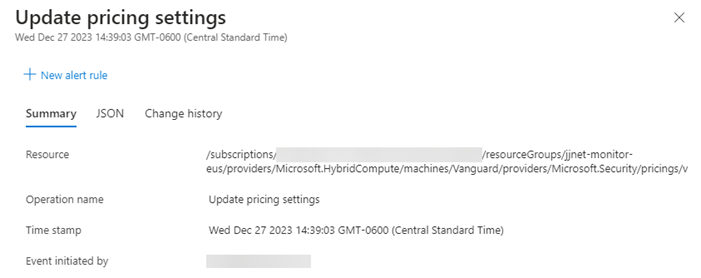
Figure 3 – The Activity Log of a targeted server will have an entry like this after running the PowerShell script.
Reversing resource level enablement of DfS
Microsoft has not yet provided a scripted method of reversing resource level enablement of DfS after you run the PowerShell script. You will need to use the REST API to affect a Delete action against the Defender for Cloud pricing configurations you created using the PowerShell script.
Tip: I was able to ‘hack’ a modified ‘delete’ version of the PowerShell script by changing each:
“Invoke-RestMethod -Method Put”
action in the original script to:
“Invoke-RestMethod -Method Delete”.
 If you are a stakeholder in a hybrid IT estate, you owe it to yourself to learn about Azure Arc, get a copy of my book: (co-authored by Microsoft’s Steve Buchanan)
If you are a stakeholder in a hybrid IT estate, you owe it to yourself to learn about Azure Arc, get a copy of my book: (co-authored by Microsoft’s Steve Buchanan)
Azure Arc-Enabled Kubernetes and Servers: Extending Hyperscale Cloud Management to Your Datacenter
https://www.amazon.com/Azure-Arc-Enabled-Kubernetes-Servers-Hyperscale/dp/1484277678
Tags: #MVPBuzz #HybridCloud #CloudSecurity #DefenderForCloud #AzureArc #AzureHybrid #AzureVM #VMSS #DefenderForServers
