Azure Sentinel users: enable these new Analytics rules announced in the Microsoft Security Response Center (MSRC) post: Customer Guidance on Recent Nation-State Cyber Attacks – Microsoft Security Response Center. No need to download or import rules: Microsoft has released the rule templates to all customer Azure Sentinel workspaces and they are ready for you to enable.
Microsoft has published several detections to Azure Sentinel that provide additional signals for post-compromise techniques observed in these intrusions. These Azure Sentinel rules are recommended defenses among many others listed in the MSRC post. Figure 1 shows what these new rules look like in the Azure Sentinel console (Configuration -> Analytics -> Rule Templates).
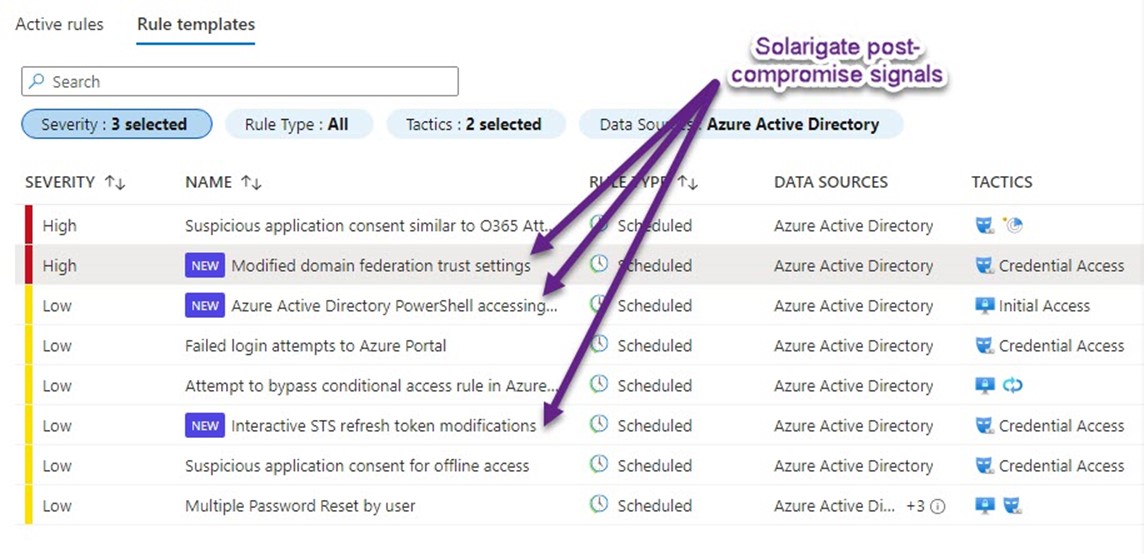
Figure 1 – Locate the new analytics rules by filtering for severity High & Low, data source Azure Active Directory, and tactics Credential Access and Initial Access
To enable the rules in your Azure Sentinel instance, select each new rule template one at a time. Push the Create rule button in the lower-right of the details pane for the selected rule.
The data source for these analytics rules is Azure Active Directory. Since there is no cost or license needed to enable the Azure Sentinel connector to Azure AD, every Azure Sentinel customer should be using this connector. As a best practice, these rules should be enabled in most Azure Sentinel deployments immediately.
Microsoft response to Solarigate has been strong and immediate, read more at: Microsoft unleashes ‘Death Star’ on SolarWinds hackers in extraordinary response to breach (msn.com).
Tags: #MVPBuzz #AzureSentinel #securityManagement #SIEM #Solarigate #MSRC
