Situation: You have an Azure VM running Windows Server that you need to access via RDP over the Internet, and you are, per best practice, changing the well-known RDP port of 3389 to a random high-numbered port. This will significantly reduce the brute-force attempts of hackers and hostile bots to break in via RDP.
Problem: In the process of configuring the necessary changes, you lose your ability to RDP to the VM. Retracing your steps:
- You added the high-numbered port to your Azure public IP network security group as an allowed Inbound rule.
- You modified the TCP port used by RDP to match and restarted the VM. (Procedure: https://support.microsoft.com/en-us/help/306759/how-to-change-the-listening-port-for-remote-desktop)
What did you forget? The Windows firewall on the VM! It’s still blocking your new port number from the Internet network interface of the VM. What to do…redeploy the VM and start over?
There is now a very quick and easy way to ‘push’ Windows Firewall modifications to your VM from the Azure Portal. This is the Run Command feature of Azure VMs: https://docs.microsoft.com/en-us/azure/virtual-machines/windows/run-command
You can use familiar PowerShell to modify the Windows Firewall by adding rules: https://blogs.technet.microsoft.com/heyscriptingguy/2012/11/13/use-powershell-to-create-new-windows-firewall-rules/
Solution: Use the Run Command Script feature to open the Windows Firewall on TCP port 21210 (an example random high numbered port). Paste this command into script line 1 in the Virtual Machine -> Operations -> Run Command Script and press Run.
New-NetFirewallRule -DisplayName “MyRDPPort” -LocalPort 21210 -Protocol ‘TCP’ -Action ‘Allow’ -Enabled ‘True’
You will have access to your Azure VM in seconds. Figure 1 shows successful execution of this PowerShell command.
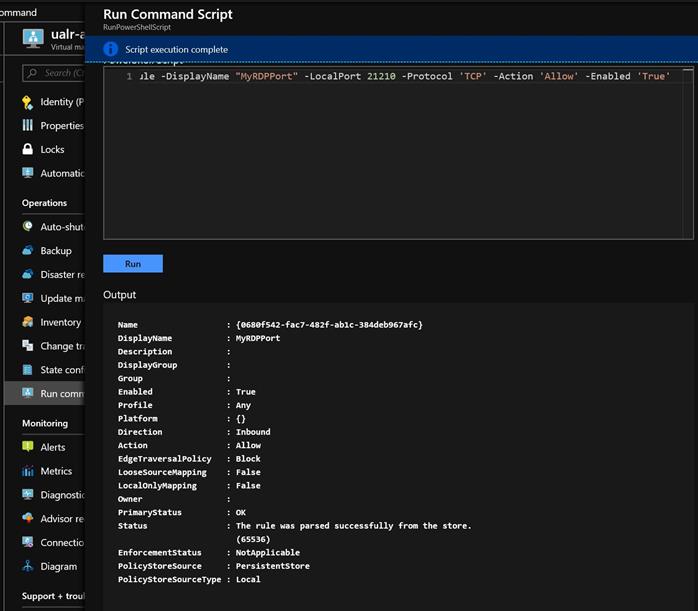
Figure 1 – Successful run of command line to open a port in the Windows firewall
Tags: #MVPBuzz #Azure #AzureVM #Scripting #AzureAutomation #PowerShell
